Full
Disk Encryption (FDE)
versus
File Encryption Technologies
A
White Paper Excerpt
By Howard Lubert
Contributing
Analyst
Security, identity theft, corporate espionage and a litany of similar issues are at the heart of many companies IT strategies. The more sensitive the data the more vital the security measures. Often, in the mad scramble to erect firewalls, supplement password protocols, add antivirus and spyware protection and a very simple, yet critical concept is overlooked. That being data encryption.
Considering
the number of enterprise and small business users who are using laptops as
a primary computer system we thought it essential to shed some light on this
subject for our readers. We are posting this month an excerpt from a white
paper authored by one of our contributing analysts, Howard Lubert, which will
help clarify some of the issues related to this significant threat to data
security.
~ED~
Introduction
Full-disk encryption products are designed to meet the threat of data compromise through the loss or theft of laptop or desktop computers. They provide a greater level of security than file encryption products, by encrypting all data, and providing user-authentication at boot-time. File encryption products may be bundled with an operating system, and can provide data separation functionality -though this can come at the cost of greater complexity, and lower security. This paper discusses the principal issues relating to selecting a data encryption technology.
Background
Full-disk encryptors (FDEs) encrypt all data on a machine's hard drive. This includes the entire operating system, all applications, and any user data. To achieve this, an FDE contains components that are independent of the operating system, and execute before the operating system is loaded. These components are responsible for authenticating the user when the machine is booted, and providing low-level encryption.
An FDE will typically include a component that works with the operating system, referred to as a protected-mode driver. The driver is responsible for ensuring that the encrypted disk appears as normal to the operating system, allowing all encryption and decryption to remain transparent to the user.
File encryption products, on the other hand, allow a specific set of files or folders to be encrypted. These typically work within the operating system by implementing a filter-driver. Filter-drivers intercept access to specific files, allowing files specified by the user to be encrypted or decrypted 'on-the-fly'.
Functionality
The technical differences between encryption technologies dictate their appropriateness for specific threat models. The FDE is a simple and effective solution for protecting a machine's data in the event of loss or theft. Its two characteristics ensure this (boot-time authentication and complete encryption). File-encryption solutions do not lend themselves towards the same threat model, as they contain no inherent authentication and are typically reliant on the user 'logon' process. There are a number of well-known attacks and publicly available tools designed to gain access to a machine in the absence of a user password. Failing this, a machine's hard-drive may be removed and mounted elsewhere, rendering even protected data vulnerable (see Security below).
A more appropriate threat-model addressed by File-encryption solutions is data separation: when a user of a shared machine is logged on, he/she cannot access another user's data, and vice versa. This cannot be achieved with an FDE solution alone, as all data becomes available to applications once a user is logged on.
However, data separation functionality is often compromised by some File-encryption implementations (such as OS bundled implementations) by:
- Allowing
existence of an agent (administrator) who can access
everyone's data;
- Not
encrypting data transmitted to or from mapped drives (server-based);
- Not working at a sufficiently low-level (See Security below).
Usability
A security system is only as good as its weakest link, and the weakest link of most good security systems is the user. Systems should be designed so that they are used, and are easy to use. FDE solutions offer the advantage of being transparent to the user, and providing mandatory security. File encryption solutions do not offer mandatory security, as each new folder is required to be marked for encryption. Additionally, users are required to remember to save sensitive data to the correct folder.
Where the File-encryption solution is not part of the OS, the user will be required to use a custom application to specify folders or files for encryption, so ultimately the level of usability is in the hands of the solution provider. Where the solution is part of the OS, the onus can be placed on the system administrator. However, this introduces a security implication, as the administrator acts as an agent with access to the encrypted data. Thus if data separation were the objective, there is a potential compromise.
As File-encryption solutions do not typically provide user authentication, their ability to enforce security becomes dependent upon authentication performed separately. However, the majority of security concerns centre around their inability to encrypt the operating system. Operating systems typically include a paging file to which data is 'swapped' by the memory manager. Consequently, sensitive data may be encrypted in one place, but left in plain-text elsewhere1 Some operating systems provide the ability to request that the paging file to be wiped on shut-down, though this is difficult to enforce, and cannot cater for abrupt power-downs. . A similar security threat is posed by common applications that regularly store data in 'temporary' files. It may be possible to select for encryption of temporary files under some circumstances. However, where this is possible, the complexity of the solution deployment is increased.
By
operating above the file system, File-encryption products can be vulnerable
to file-system quirks. An example being an encrypted file's original plain-text
contents being left on disk and marked as erased.
1 Some operating systems provide the ability to request that the paging file
to be wiped on shut-down, though this is difficult to enforce, and cannot
cater for abrupt power-downs.
File system filter drivers can potentially be un-loaded or replaced. Whilst this would typically require administrative privileges, a successful attack would leave the user of a File-encryption product unknowingly saving sensitive data in plain-text. A similar attack to an FDE would at best result in a denial of service.
In
summary: File-encryption products are partially dependent upon the nature
of the operating system and the applications with which they interact. For
FDEs there are no such dependencies. If an FDE has been implemented correctly,
the security of the product is dependent upon the security of the algorithm
used. Thus data recovery by an attacker can take in the order of thousands
of years.
Common
Factors
A number of security-related factors may be better described as product dependent as opposed to encryption technology dependent, and may be offered by either FDE or File-encryption implementations. Principal amongst these are token support and key management.
Security can be provided through the use of physical tokens such as smart cards or USB tokens. Token-based solutions introduce the 'something you have and something you know' security model. This allows additional security through secondary authentication, and allows data sharing amongst groups, as tokens can be programmed with common keys.
Tokens
can provide a convenient mechanism for secure distribution of encryption keys.
However, irrespective of token use, a product should support key management
to allow secure distribution and archiving of key material. A disadvantage
of OS bundled encryption solutions is their inability to generate and manage
strong encryption keys with sufficient randomness to maximize the security
of the algorithm.
Overview Summary
FDEs
and File-encryption products differ in both functionality and security, predominately
as a result of their 'relationship' with the operating system. FDEs provide
a greater level of security, and a simple solution to the threat of data loss
or theft. File-encryption products provide data separation functionality,
and may be bundled with the operating system. The differences in encryption
technology place differing emphases on usability, transparency and mandated
security, however the technologies may be regarded as complimentary where
application requirements are sufficiently broad.
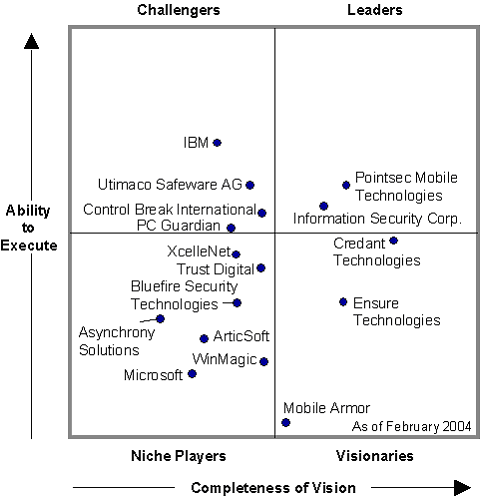
The Gartner Magic Quandrant of players in this space follows:
High Level Comparison of FDE Products
We
examined a number of FDE product sets (see the accompanying chart on security
and encryption details) such as Synet's suite of products, Secure Send, Tracker,
and PC-Keeper. The Synet Tracker solution was, in our opinion, a best of breed
solution in this space and has the added feature of providing a "LoJack"
component if the user cannot correctly enter the password at the challenge
- response queue.
Many of these products do not invest the time, money or resources to acquire
PHIPS certification for these products unless they have a distinct government
market strategy. We did see some off-shore developed products with PHIPS equivalent
type certifications such as CESG, DCSA, DIPCOB and GCAT in the United Kingdom.
Our research of the marketplace indicates that the lack of a PHIPS certification
is only a barrier to participation in the aforementioned government market.
The Bottom Line
Corporate users of all sizes should carefully evaluate their encryption requirements before selecting a product. We believe that, if a machine is not shared between users, an FDE solution is by far the best overall way to maximize the data that resides on the machine's hard disk drive. While all of these solutions take some overhead and system management the level of security is well worth the minor performance hit vs. having inadvertant access to all of your company's secrets out there for the offing.
Howard Lubert is the Managing Partner and Senior Analyst at SafeHatch LLC in Wayne, Pa.
Questions or comments? E-mail editor@int2.com







